Cisco Unified Communications Manager – Secure LDAP
Expanding a little bit on our previous post CUCM LDAP Active Directory Integration-Sync and considering Microsoft advisory ADV190023 which makes Secure LDAP (LDAPS) mandatory, we will discuss the additional steps to configure Secure LDAP over port 636.
Upload the Active Directory (AD) certificate.
If you do not have the certificate, you can either obtain it form the AD server directly or using open-ssl with the command openssl s_client -showcerts -connect <host>:636.
Once the certificate is ready, go to Cisco Unified OS Administration > Security > Certificate Management and click on Upload Certificate.
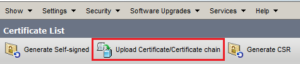
Select tomcast-trust and the correct certificate and click Upload.
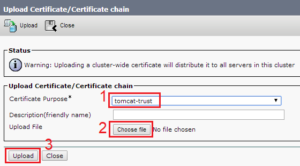
Once the upload is completed, from the CLI restart the Tomcat service with the command utils service restart Cisco Tomcat.
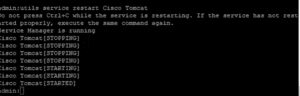
Configure/Update LDAP Authentication and LDAP Directory to use SSL.
Update the Host Name for Sever (the name MUST match the CN field of the certificate).
Set the LDAP Port to 636.
Check the Use TLS box.
Same steps for LDAP Directory if it is being used.
NOTE: If there will be more than one LDAP server configured the certificate will have to be discovered and noted for all of them.

I am a Cisco Certified Network and Collaboration Engineer (CCNP) with over 9 years of experience and a passion for all things technology. I have spent most of my time mastering the world of networking and collaboration, but still find myself dabbling in cloud computing and programming.
Solving problems and learning something new in the process is my favorite part of the job. Having a depth understanding of the technology is what has driven my success.

Are we able to issue our own SSL Certificates, like using OpenSSL, for Cisco Collab products?
We’re using them of course for CUCM, because they allow wildcard certs, but for UCCX and Finesse? As well as Cisco CER?
Could I generate my certificates in our OpenSSL server, like we do for many other devices (non-cisco, etc)…
I already have a tomcat trust by the very nature of having a CUCM and active Directory relationship. Do i need to upload another server certificate specifically for the LDAPS up grade?