Cisco ASA – Cisco AnyConnect with DUO Multi Factor Authentication
Recently i though to deploy Cisco ASA in my lab and try Multi Factor Authentication with Cisco owned DUO app.
After installing Cisco ASA and complete the basic configuration, i started with DUO configuration on ASDM and DUO Admin (Website).
First and the foremost you need to have an account in DUO portal (I did register a trial version). After registering, i downloaded DUO app on my mobile phone as well so that my primary account from where i do login as Admin, is also authenticated with MFA.
- Register for a Duo account.
- Login to Duo Admin Panel
- Navigate to Applications
- Click on Protect an Application and search for Cisco ASA SSL VPN
- Click on Protect
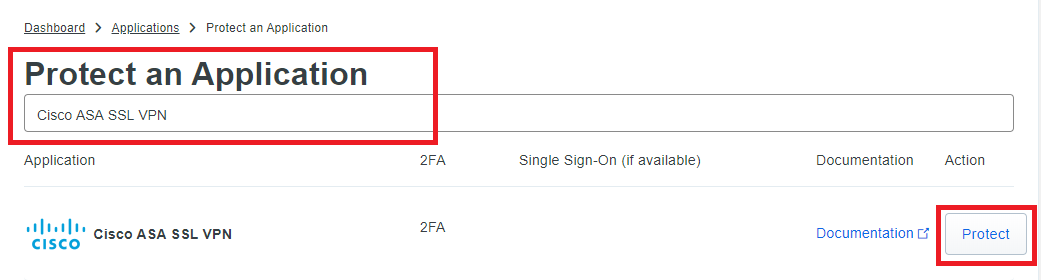
- You will be redirected to the application page. Here are the things you need to do:
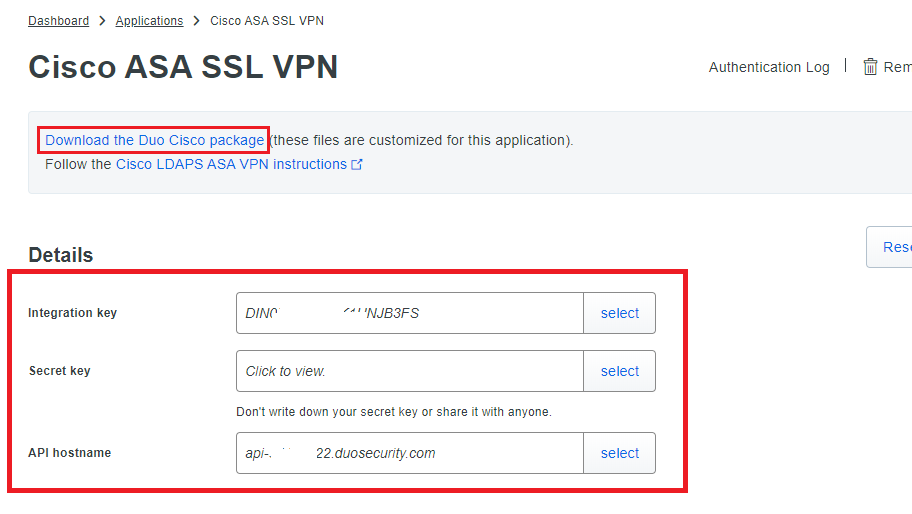
Downloading Cisco DUO JS Package and DigiCert CA Certificates
- Download the Duo Cisco package from Cisco SSL VPN application page, and unzip it and save the file in your desktop.
- Download the following certificates from Cisco ASA LDAP page and save it in your desktop.
- DigiCert High Assurance EV Root CA
- DigiCert SHA2 High Assurance Server CA
So, all the three files will look as below: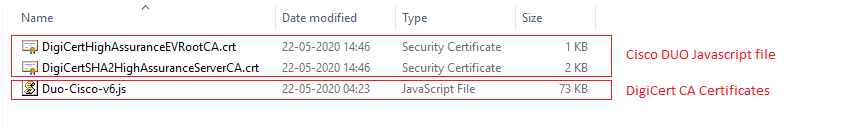
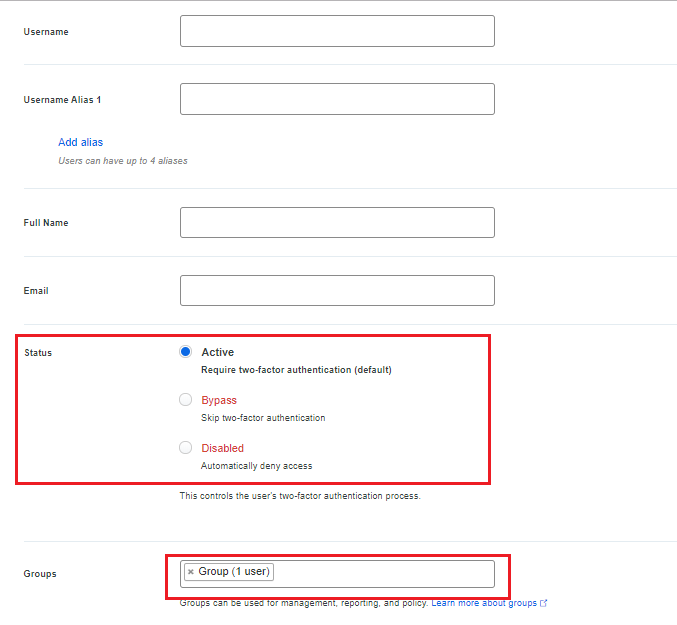
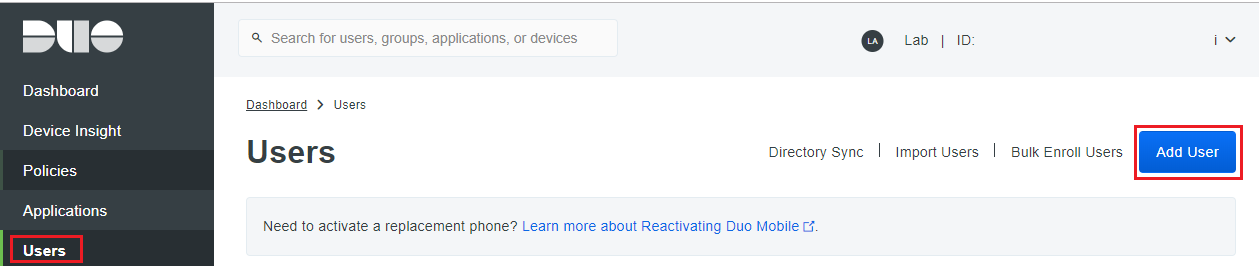
Register a user in DUO
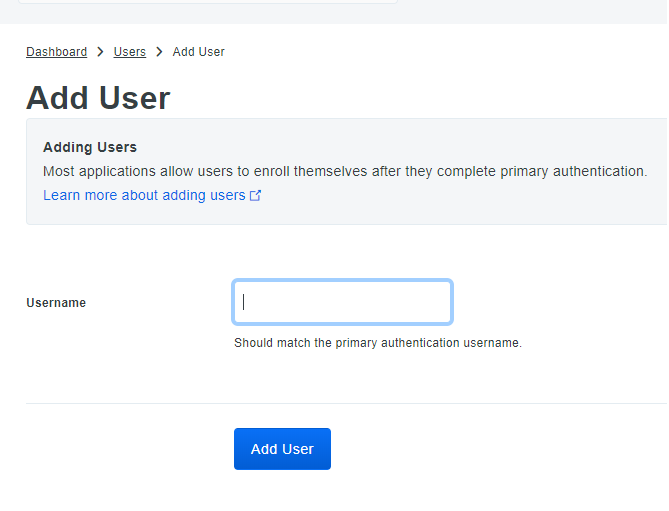
- Navigate to Users > Click on Add User
- Username > Enter a username. The username should be the same name as configured in your AD, who is going to authenticate himself/herself using Cisco AnyConnect VPN.
- Make sure that the user is part of a group and the user is Active.
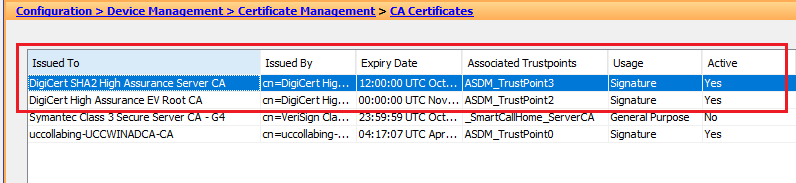
Install the DigiCert CA Certificates
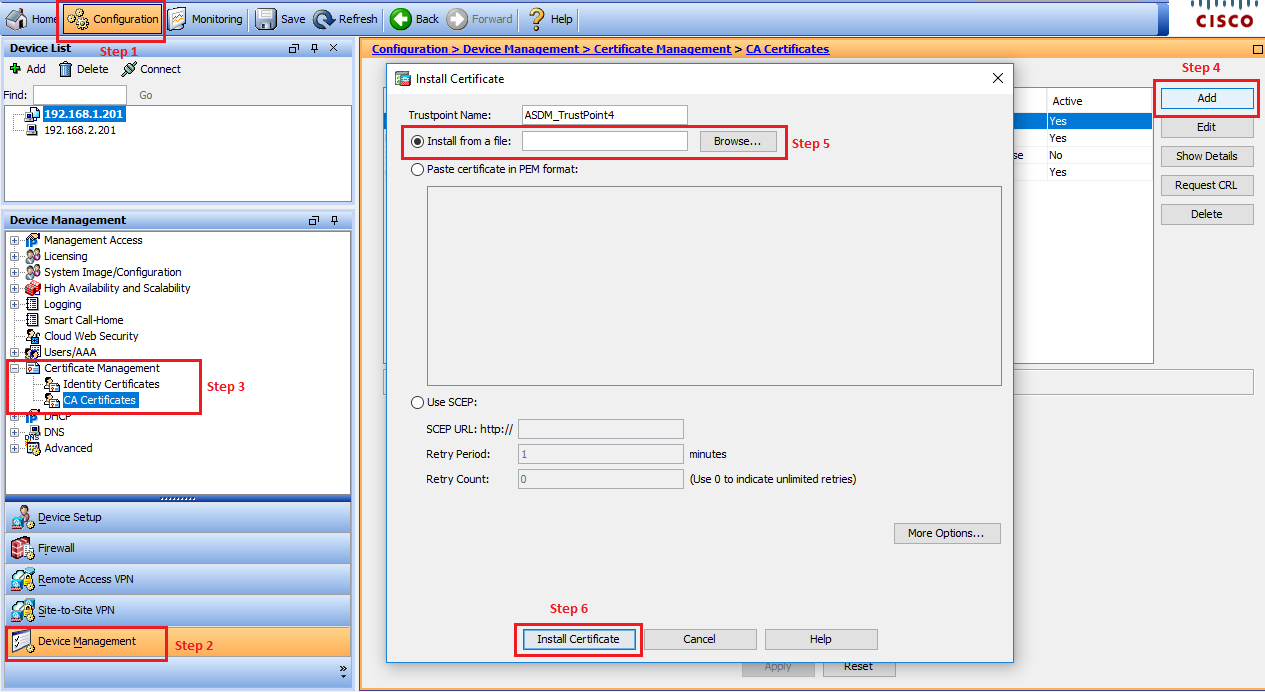
- Log on to Cisco ASDM Interface.
- Click the Configuration tab and then click Device Management in the left menu.
- Navigate to Certificate Management > CA Certificates.
- Click the Add button.
- In the “Install Certificate” window, select the Install from a file option and then click the Browse.
- Select the DigiCert High Assurance EV Root CA file you downloaded from DigiCert and click on Install.
- Select the DigiCert SHA2 High Assurance Server CA file you downloaded from DigiCert and click on Install.
Modify the Login Page
Importing the JS File
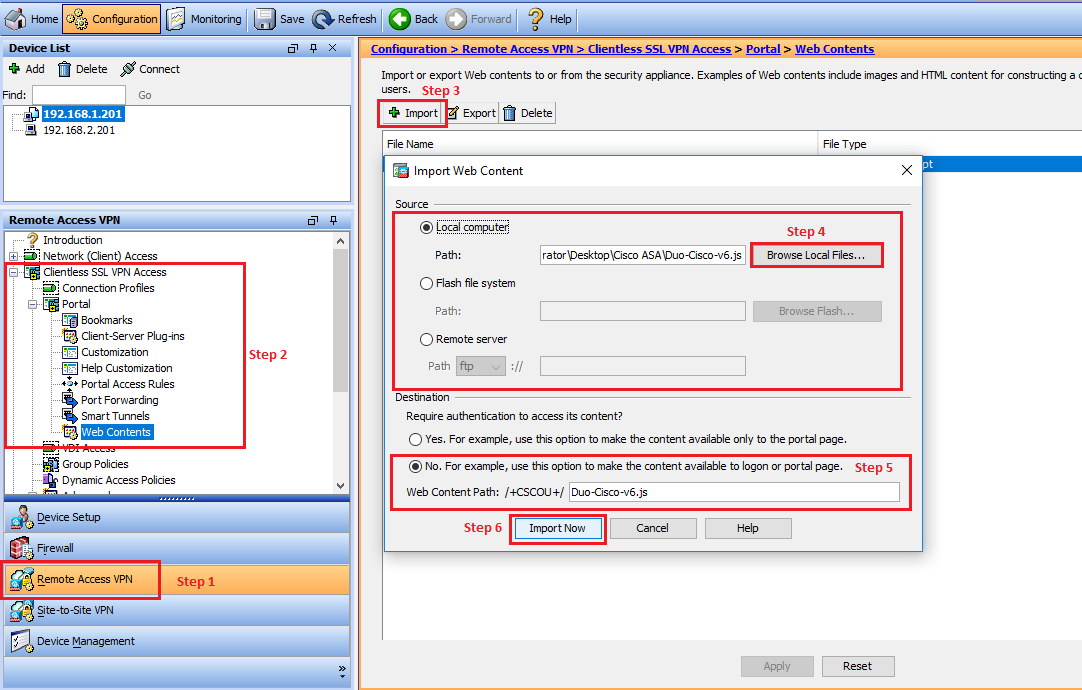
- Click the Configuration tab and then click Remote Access VPN in the left menu.
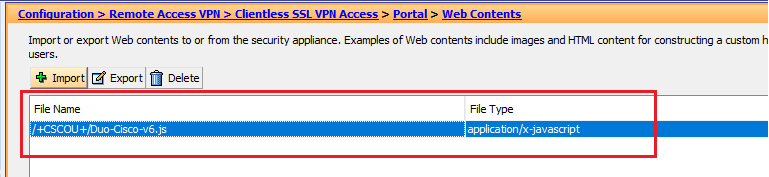
- Navigate to Clientless SSL VPN Access > Portal > Web Contents.
- Click on Import.
- Select Local computer, click Browse Local File. Upload the JS file Duo-Cisco-vX.js file you downloaded and extracted from the zip file.
- After the file is selected, Duo-Cisco-vX.js will appear in the Web Content Path box.
- In the Destination section, select No in response to “Require authentication to access its content?“
- Click on Import Now
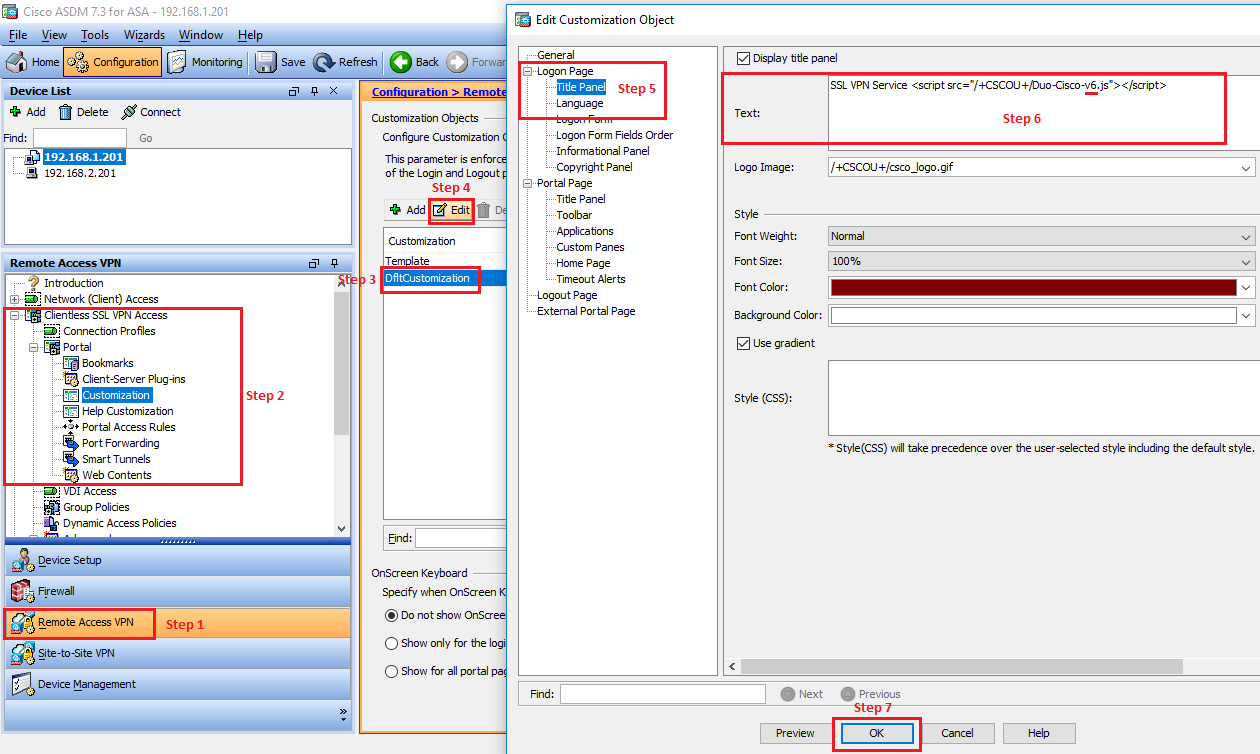
Customizing the Login Page
- Navigate to Clientless SSL VPN Access > Portal > Customization
- Click on Edit
- Click Title Panel (under Logon Page)
- Type <script src=”/+CSCOU+/Duo-Cisco-vX.js”></script> (replace vX with the file version you downloaded in the previous step)
- Click OK.
- Click on Apply.
Configuring the DUO LDAP Server
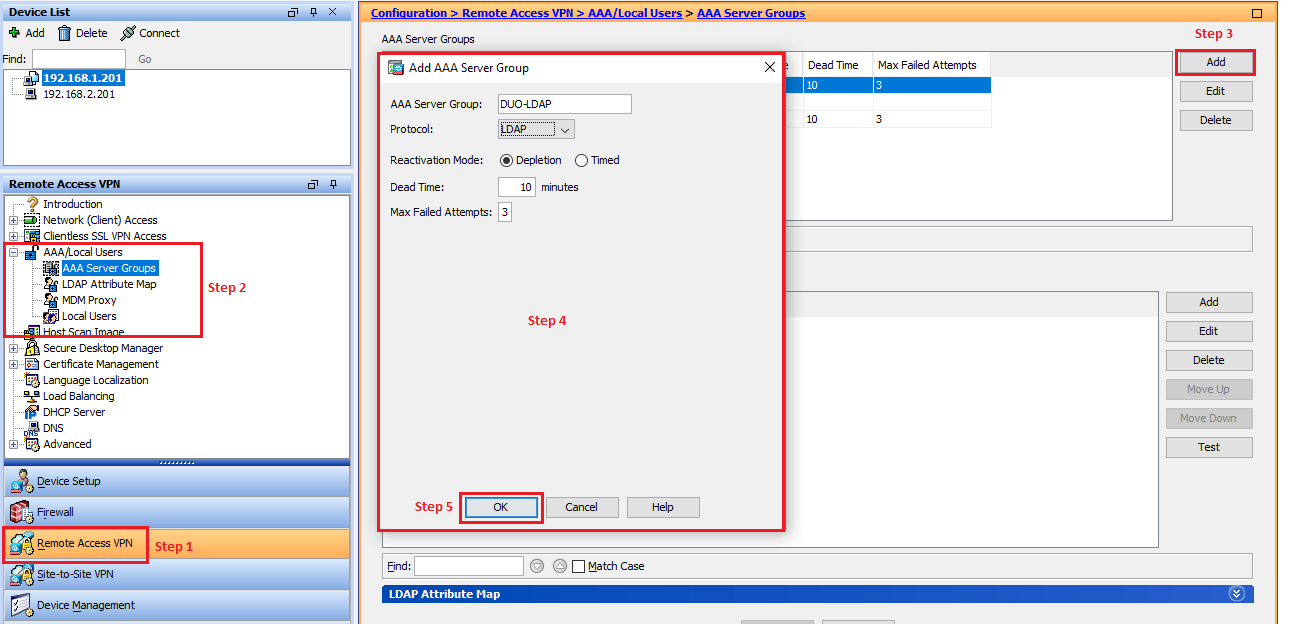
Configuring AAA Server Group:
- Navigate to AAA/Local Users > AAA Server Groups
- Click Add
- In the Server Group > Duo-LDAP
- Protocol > LDAP
- Click on OK
Add AAA Server
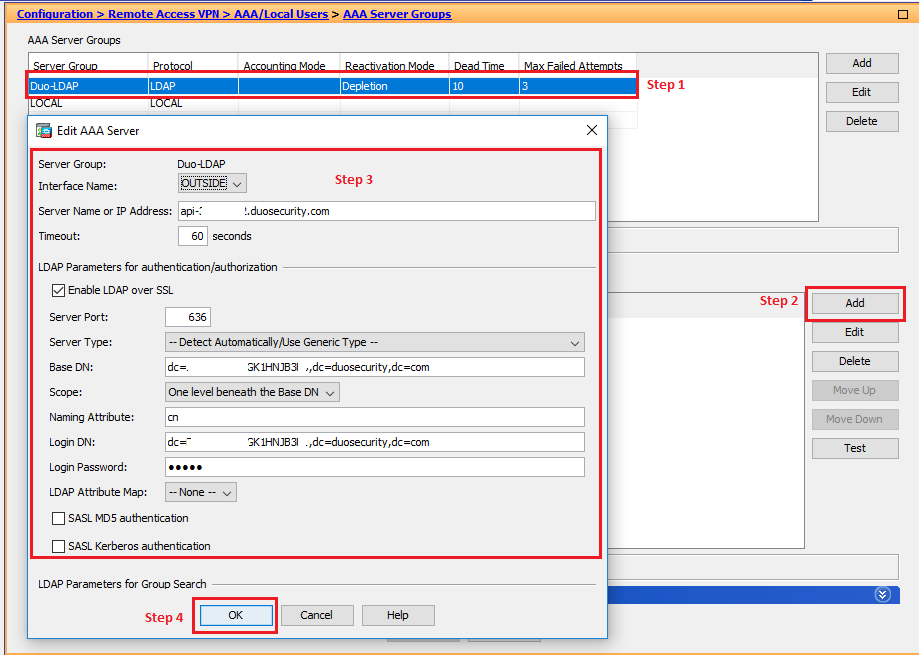
- Select the DUO-LDAP group which was just added.
- Interface Name > Choose the external interface which is connected towards Internet.
- Server Name or IP Address > Your API hostname (i.e. api-XXXXXXXX.duosecurity.com)
- Timeout > 60 seconds
- Check Enable LDAP over SSL
- Server Port > 636
- Server Type > — Detect Automatically/Use Generic Type —
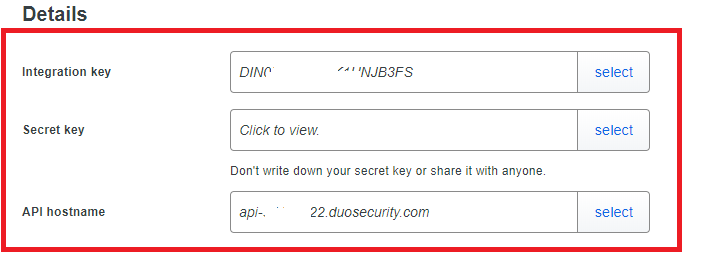
- Base DN > dc=INTEGRATION_KEY,dc=duosecurity,dc=com
- Scope > One level beneath the Base DN
- Naming Attribute(s) > cn
- Login DN > dc=INTEGRATION_KEY,dc=duosecurity,dc=com
- Login Password > SECRET_KEY
- Click on OK
- Click on Apply
Note: Replace INTEGRATION_KEY and SECRET_KEY with your application-specific keys)
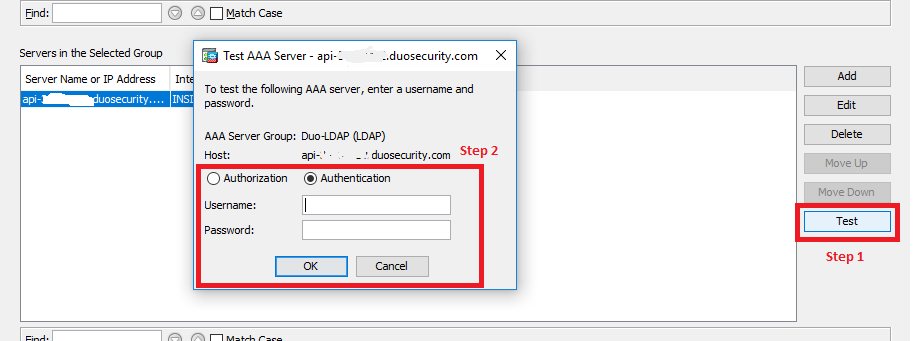
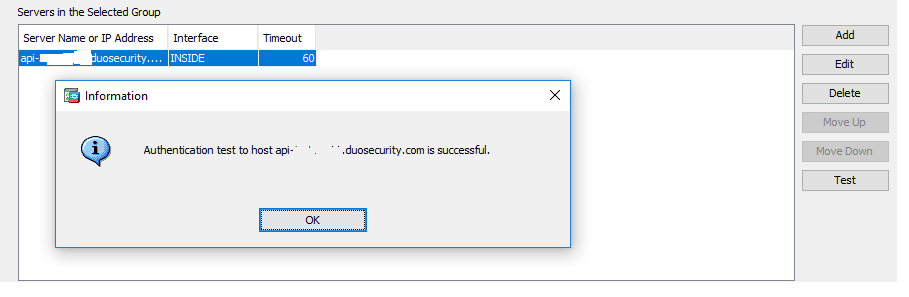
Testing AAA Server Authentication
- Click the Test button.
- On the “Test AAA Server” form, select Authentication.
- Enter the username of user that exists in Duo and has a valid authentication device (like a phone or token).
- Instead of entering the user’s password, enter the passcode from Duo Mobile App and then click OK.
Configuring the DUO LDAP Server
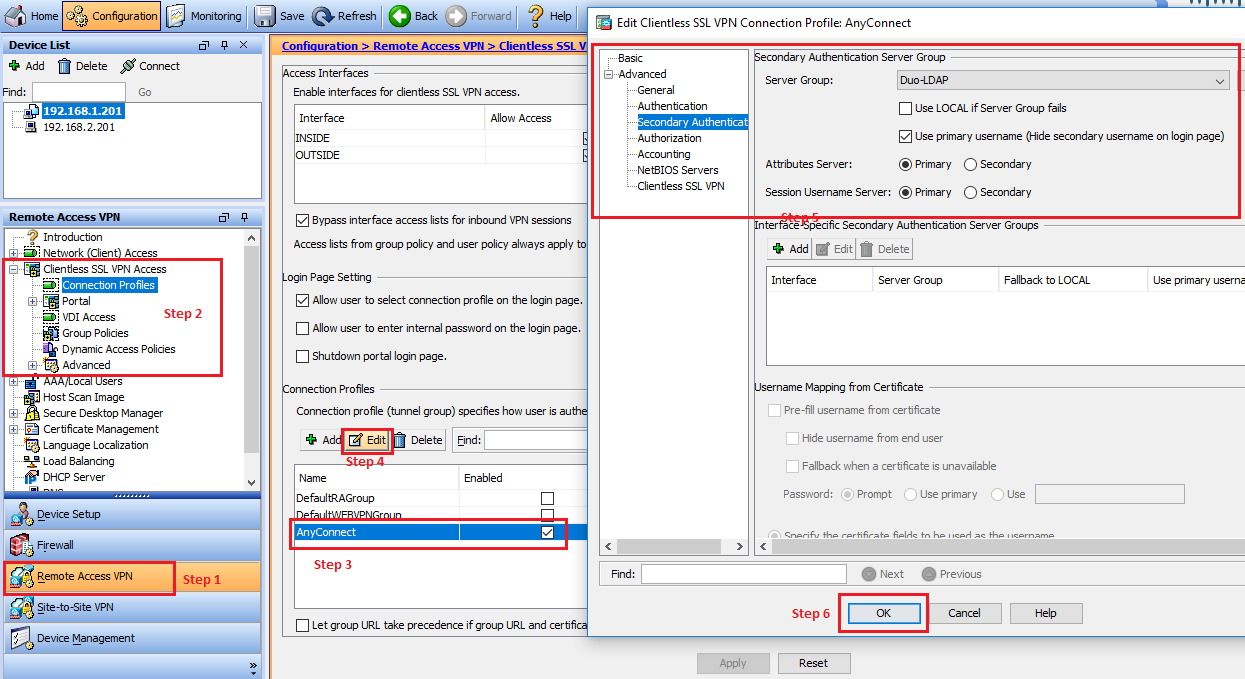
- Navigate to Clientless SSL VPN Access > Connection Profiles
- Select the connection profile to which you want to add Duo Authentication near the bottom and click Edit
- Choose Secondary Authentication (under Advanced) from the left menu.
- Select Duo-LDAP from the Server Group list.
- Uncheck the Use LOCAL if Server Group fails check box.
- Check the Use primary username check box.
- Click OK
- Click Apply
Testing with DUO – Using WebPage and AnyConnect VPN Client
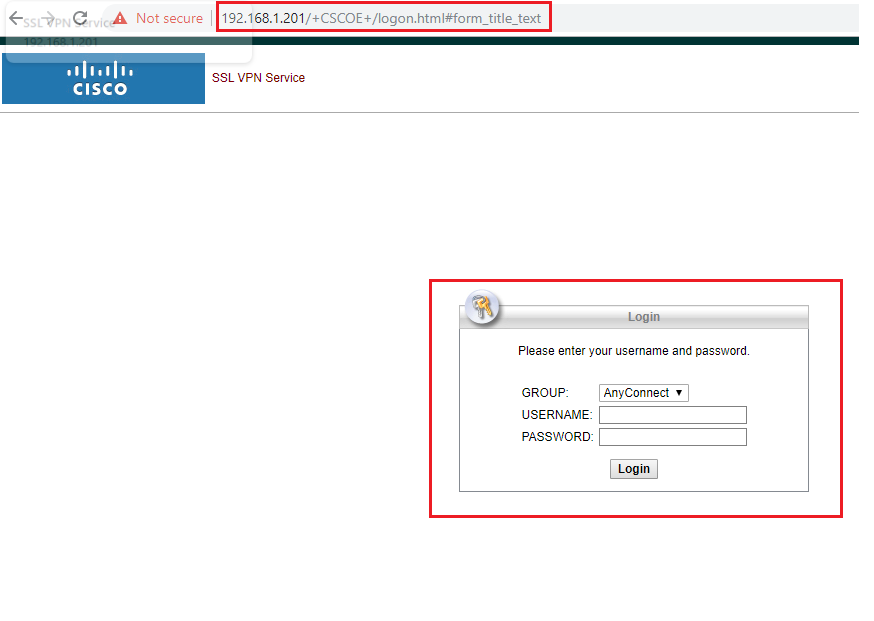
Testing using WebPage
- Enter the Web URL of Cisco ASA
- You will be prompted to login with two way authentication. On the first page, the authentication will be you RADIUS Authentication (Local Authentication).
- Enter your username and password and click on Login.
- Once you successfully authenticate on your first page, then you will be asked for secondary authentication i.e., DUO Authentication where you can either send a push notification and approve the authentication or enter the generated password from your Mobile DUO app.
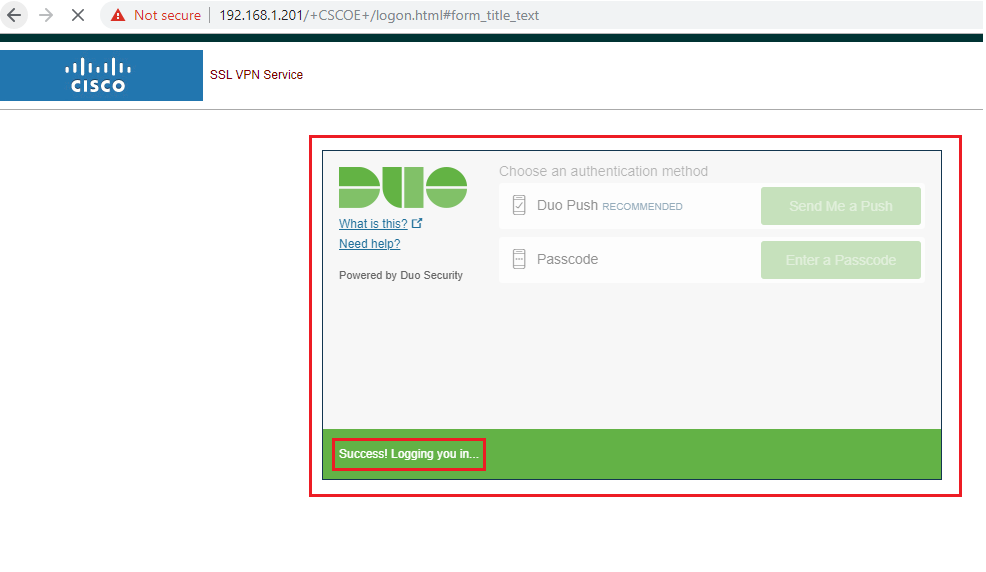
Testing using Cisco AnyConnect Client
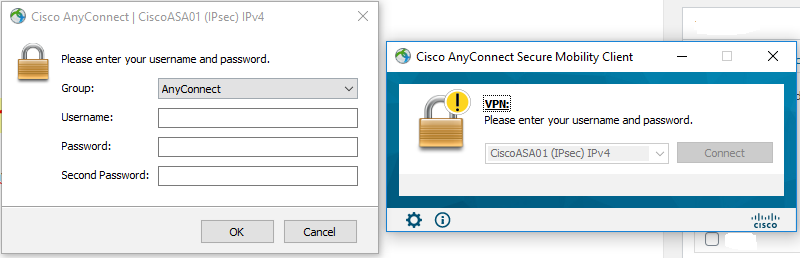
- Launch Cisco AnyConnect Client and connect to your ASA
- Enter your AD Username
- Enter your AD Password
- Enter your secondary Password : You can get the passcode from your DUO App
- Click on OK
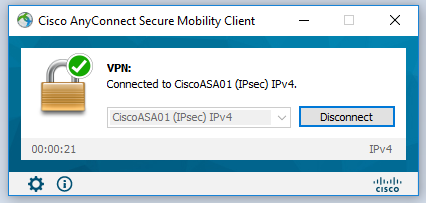
- If your AD username and password and your secondary authentication is successful, you will be able to login to Cisco AnyConnect VPN.

I am working in an IT company and having 10+ years of experience into Cisco IP Telephony and Contact Center. I have worked on products like CUCM, CUC, UCCX, CME/CUE, IM&P, Voice Gateways, VG224, Gatekeepers, Attendant Console, Expressway, Mediasense, Asterisk, Microsoft Teams, Zoom etc. I am not an expert but i keep exploring whenever and wherever i can and share whatever i know. You can visit my LinkedIn profile by clicking on the icon below.
“Everyone you will ever meet knows something you don’t.” ― Bill Nye